Data Watch
Data Watch is designed to allow you to quickly and easily audit the destinations that your site is sending data and get notified as soon as new ones are detected. Useful for being alerted about Magecart style attacks and other data exfiltration scenarios, you can get started with Data Watch easily.
Getting Started
If you already have a CSP setup on your site, either in Enforce mode or Report-Only mode, you can get started with Data Watch in just a few seconds. Head to the Data Watch menu item located under the CSP menu in your account. Here you can see any sites you're currently monitoring for data egress or add a new site to monitor.
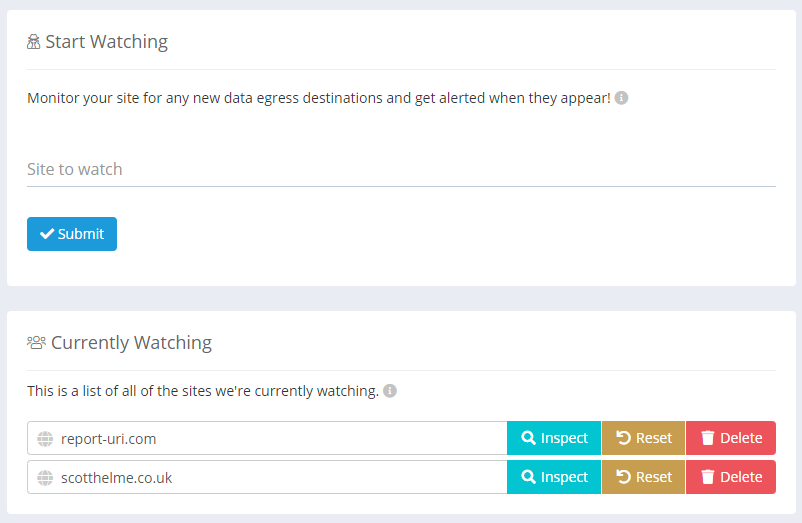
We allow granular control of the sites you wish to monitor and as an example, www.report-uri.com and blog.report-uri.com would be two different sites and monitored/alerted separately from each other. This means you can setup monitoring and only receive alerts for the areas of your site that interest you.
If you add a new site to be monitored by Data Watch, we will start analysing all inbound reports for that site to audit your data egress and send alerts when new destinations are detected. Data egress destinations for any given site can be viewed by clicking the Inspect button.
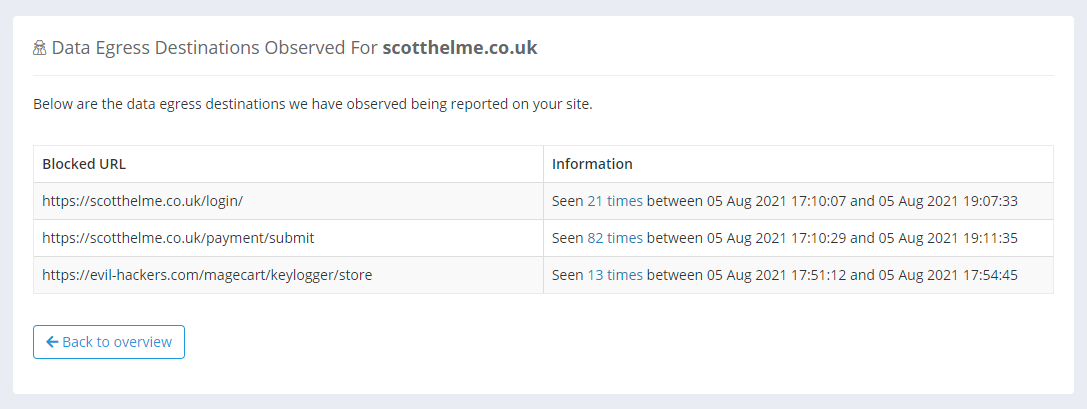
This will show all the data egress destinations we have detected for your site.
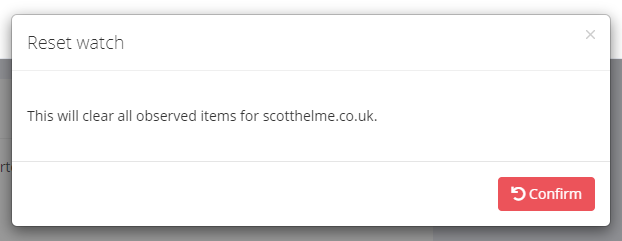
The Reset button will clear our list of destinations and start the monitoring process again. This may be helpful if you've made changes to your site and would like to rebuild a fresh list of your destinations.
The Delete button will delete the site from Data Watch, removing all data with it, and will stop ongoing monitoring and alerting for this site.
Data Watch Setup
If you do not have an existing CSP on your site, there are several ways you can get started with Data Watch.
If you would like to build a fully functional CSP first, then we recommend the CSP Wizard. Once you have a CSP setup you can then enable Data Watch to monitor your reports.
If you would like to use Data Watch to audit and monitor your data egress without having to create a fully functional CSP first, there are some options. A CSP deployed in Report-Only mode can be used to audit and monitor all of your data egress on an ongoing basis with minimal effort.
Content-Security-Policy-Report-Only: default-src * 'unsafe-inline' 'unsafe-eval'; connect-src 'none'; form-action 'none'; report-uri https://{subdomain}.report-uri.com/r/d/csp/reportOnly
This policy is delivered in a CSPRO header so no blocking action will take place, but reports will be sent for all data egress on your site so that Data Watch can monitor the destinations. As it should be relatively safe to send data to your own site, you could also start with the following policy instead. Changing connect-src 'none' to connect-src 'self' and form-action 'none' to form-action 'self' will allow data to be sent to your own site, so it won't be reported.
Content-Security-Policy-Report-Only: default-src * 'unsafe-inline' 'unsafe-eval'; connect-src 'self'; form-action 'self'; report-uri https://{subdomain}.report-uri.com/r/d/csp/reportOnly
This policy will generate more reports than usual, but you can quickly reduce the volume of reports to save your monthly quota from being consumed too aggressively. By allowing any expected endpoints in your CSPRO header, reports will no longer be sent for them.
Content-Security-Policy-Report-Only: default-src * 'unsafe-inline' 'unsafe-eval'; connect-src 'self' comment-system.com; form-action 'self' payment-provider.com; report-uri https://{subdomain}.report-uri.com/r/d/csp/reportOnly
As we have added comment-system.com to our connect-src, a user submitting a comment on our website will no longer trigger a report. Likewise, by adding payment-provider.com to our form-action, users submitting a payment will not trigger a report either. The volume of reports sent will now be greatly reduced and ongoing Data Watch monitoring for new data egress destinations will be just as effective.
The Reporting API
If you have setup the Reporting API on your site then you can use it to send CSP reports which will continue to be monitored via Data Watch. Simply add the report-to directive to your policy as usual, there are no support considerations.
Useful Links
For more details on Data Watch, check out the launch blog post: https://scotthelme.co.uk/introducing-data-watch-detect-magecart-style-attacks-fast/